The AWS GovCloud (US) regions are designed to address the specific regulatory needs of United States (federal, state, and local agencies), education institutions, and the supporting ecosystem. It is an isolated AWS region designed to host sensitive data and regulated workloads in the cloud, helping customers support their US government compliance requirements. The available set of AWS services is a subset of the AWS ecosystem.
New Relic provides you with the confidence to deploy your most critical services on GovCloud, allowing you to monitor and observe your entire ecosystem from our platform.
The AWS CloudWatch metric stream capability isn't available on GovCloud regions.
Sugerencia
You can use Terraform to automate the process of enabling cloud integrations. Read how in the Terraform official documentation site.
Requirements
- You must have your AWS account connected to New Relic before connecting GovCloud.
- If you're using our AWS Lambda monitoring: our
newrelic-log-ingestionis not deployed in the AWS Serverless Application Repository for AWS GovCloud; it must be installed manually. For instructions, see Enable Lambda monitoring. - AWS integrations supported in GovCloud:
Connect AWS GovCloud to New Relic
To start receiving Amazon data with New Relic AWS integrations, connect your Amazon account to New Relic.
- Obtain your credentials.
- Go to one.newrelic.com > All capabilities > Infrastructure > GovCloud.
- Click on Add AWS GovCloud account.
- Give your AWS account a name, provide the credentials to connect your account, and click Submit.
- Select the Amazon Web Services to be monitored with New Relic infrastructure integrations, then click Save.
How to obtain GovCloud credentials for New Relic
From the IAM console, click Add user.
For the User name, type NewRelicInfrastructure-Integrations. For Select AWS access type, select as Programmatic access.
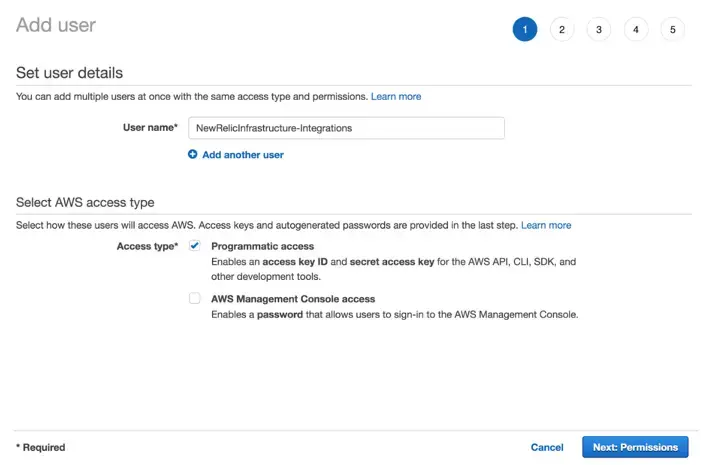
AWS IAM console > Add user: add NewRelicInfrastructure-Integrations as a user.
Attach the Policy: Search for ReadOnlyAccess, select the checkbox for the policy named ReadOnlyAccess, then click Next: Tags (adding tags is optional). Alternatively, you can create your own managed policy and limit the permissions you grant New Relic according to the AWS services you want to monitor.
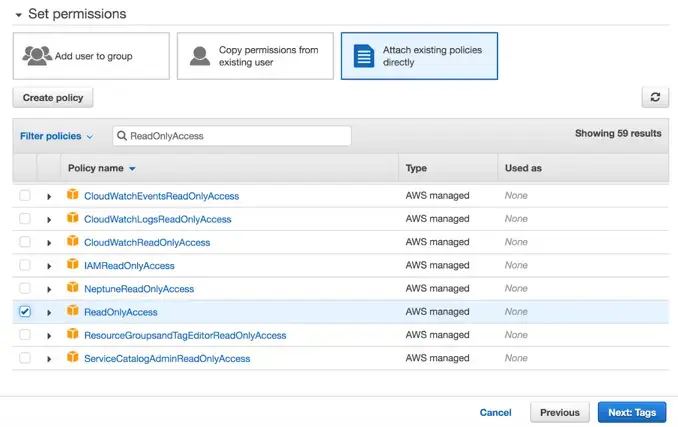
AWS IAM console > Add user > Set permissions: select ReadOnlyAccess.
On the Tags page, click Next: Review. Review the user detail summary and click Create user.
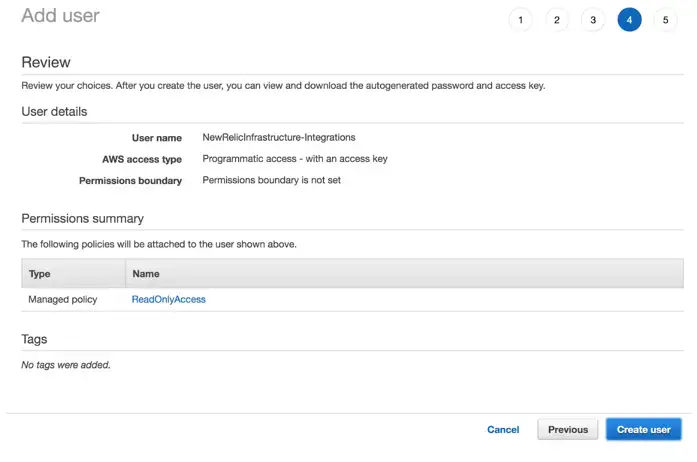
AWS IAM console > Add user > Set permissions > Tags > Review: verify that the new user information is accurate.
Your user should be successfully created. Download the user security credentials by clicking on the Download .csv button and then click Close.