You can use secure credentials with synthetic monitoring to store critical information, such as passwords, API keys, usernames, etc. This prevents scripted monitor users from viewing, updating, or deleting these values unless they have explicit permissions in New Relic.
You can set secure credentials in New Relic or with the API. The credentials are securely stored using AES-GCM 256-bit encryption at rest with keys managed by AWS Key Management Service (KMS).
To learn how to secure sensitive information in your synthetic monitoring workflows, watch this short video (3:15 minutes):
Requirements and limits
Before using secure credentials, review these requirements and guidelines:
Secure credentials | Comments |
|---|---|
Applicable monitors | The secure credentials feature is available for synthetic scripted browsers and API test monitors and step monitors. See Types of synthetic monitors for more information. |
Permissions | Account administrators can control which users can |
Limit | You can have a maximum of 1,000 secure credentials. |
Add or update secure credentials
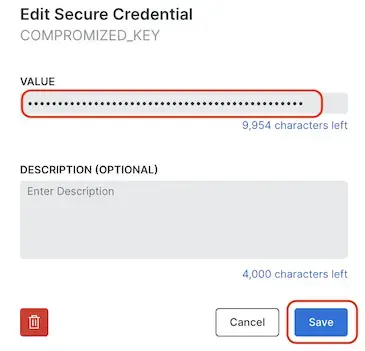
You can add or update secure credentials using the UI or the synthetic monitoring REST API. Note, values cannot be viewed, only keys.
Advertencia
New Relic recommends not to store secure credentials/keys on the Description field as it can lead to potential security issues.
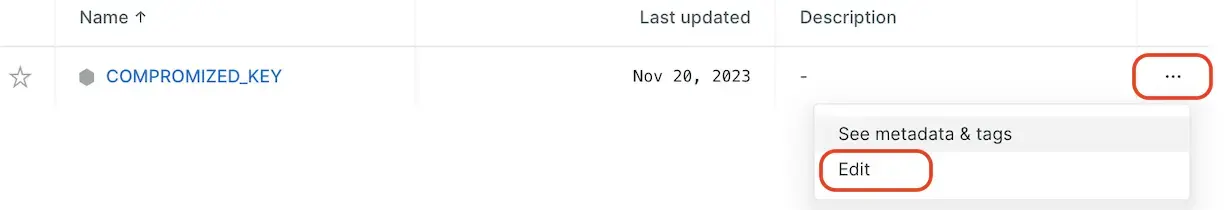
To add, view, edit, or delete a secure credential key for a scripted browser or API test monitor from the UI:
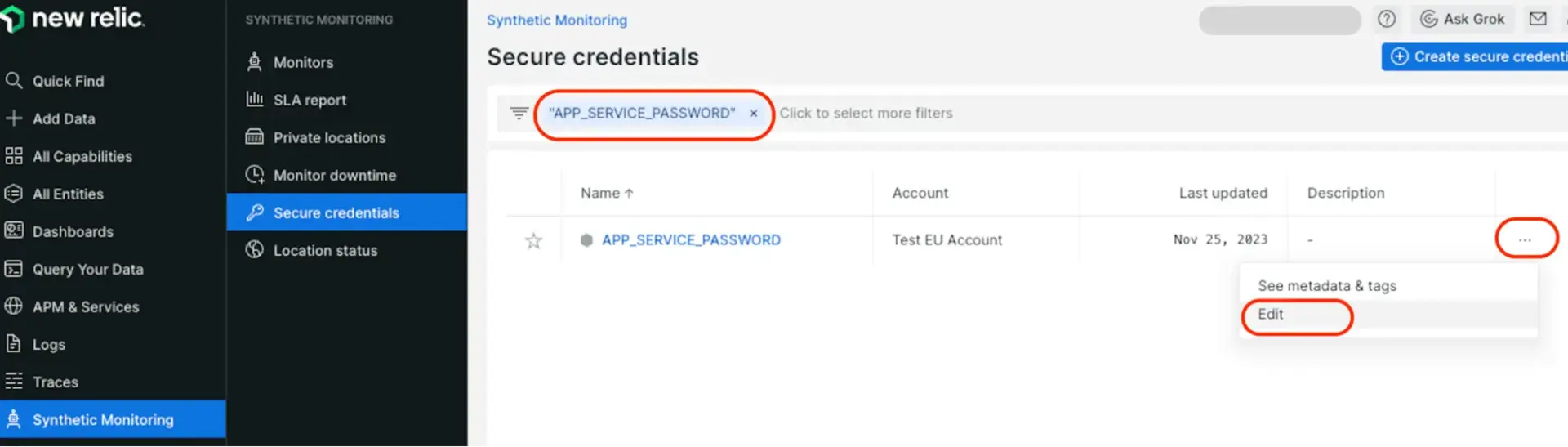
- Go to one.newrelic.com > Synthetic monitoring > Secure credentials.
- To add a new secure credential, look for the Create secure credential + button. If you have credentials already added, this button is at the top right.
- Tips for creating the Key: choose a username or other meaningful key name to identify the secure credential. Use alphanumeric or underscore
_characters. Key names must be UPPERCASE. - Tips for creating the Value: Use any combination of alphanumeric or special characters. 10000 characters maximum. This field is not accessible via the API.
- Tips for creating the Key: choose a username or other meaningful key name to identify the secure credential. Use alphanumeric or underscore
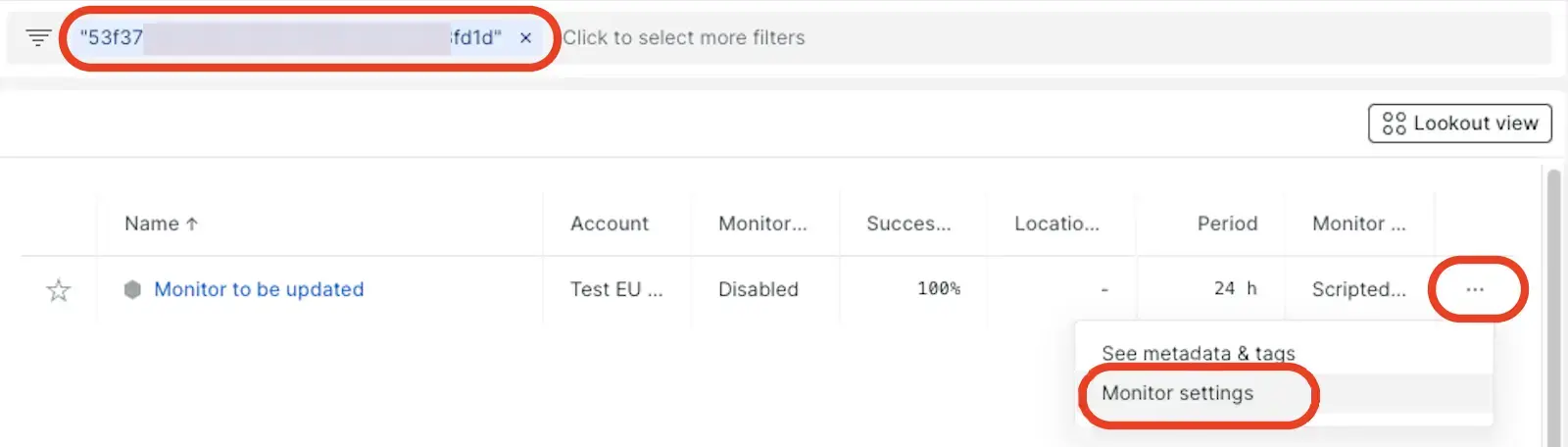
- To edit an existing credential, click the ellipsis icon for options.
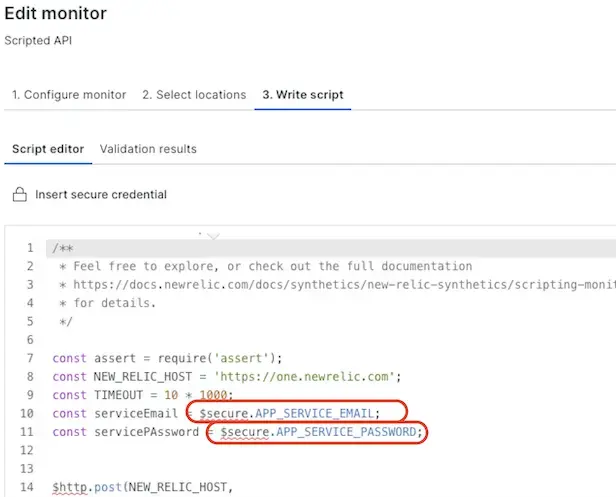
- Associate the secure credential with a scripted browser or API test by editing the script.
After you add the secure credential to the script, the Secure credentials UI shows how many scripted monitors use that credential. This number is approximate and only updates after a monitor with a secure credential has actually been run.
Sugerencia
You need to create secure credentials before you can create a monitor using them. This tip can come in handy when using an infrastructure-as-code tool like Terraform.
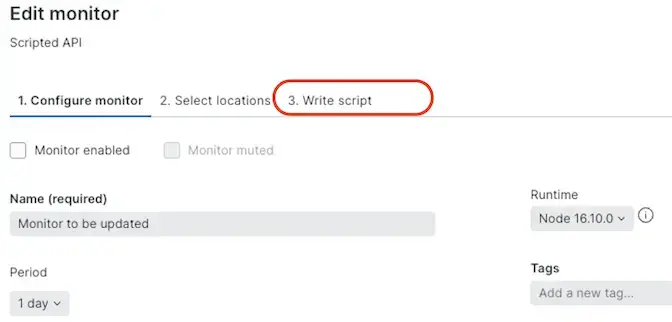
Update the script
When using the Synthetics UI editor to create scripted browsers or API test monitors, follow these guidelines:
Script | Guidelines |
|---|---|
Format | Anywhere in the script where you reference the secure credential, it is accessed via the reserved New Relic |
Existing credentials | To view or select from a list of available secure credentials:
|
Validation | To validate the secure credential, follow standard procedures to test the script or write an API test. |
Any changes to the secure credential's value will automatically take effect across all monitors that use it. You do not need to also update the script.
Exception: If you update the script and jobs are already processing, the secure credential change will not take effect until the next time the job begins.
Security for secure credentials
To ensure the security of your secure credentials, New Relic scrubs the secure value out of all data that goes to results in synthetic monitoring data and alerts. New Relic employees cannot access secure credential values and must be added to the account to be able to view secure credentials.
Example
A secure credential is named PASSWORD and the value is Pass123!. New Relic replaces Pass123! with _SECURECREDENTIAL_
For example, a script includes:
$browser.get("https://example.com/" + $secure.PASSWORD)The script results will show that your synthetic monitor went to https://example.com/_SECURECREDENTIAL_, even though it actually went to https://example.com/Pass123!. This ensures the value of the secure credential will not appear in the results.
Redacted information
We currently redact the following from the results of your monitor:
- The exact values of your secure credentials
- Any percent-encoded values of your secure credentials
Protecting your credentials in use
When creating a script, ensure that secure credentials are not passed to an external site or entered into a website in a way that causes them to be displayed or otherwise disclosed.
The protection mechanisms detailed above are designed to prevent disclosure of the credentials when stored by New Relic and in-text responses from the website being monitored. However, the scripting capability allows users to implement functionality that could result in the disclosure of the credentials if misused by the user. New Relic does not control the site being monitored or the actions of individual users of your organization. For this reason, you should only grant the "Use credentials" permission to users that are fully trusted and authorized to do so by your organization. To update permissions for secure credentials in Synthetics monitoring, please follow user management concepts to control capabilities for secure credentials.
New Relic logs instances of saving or validating monitors that include a secure credential; the logs are queryable via NrAuditEvents.